| |
|
|
Multi User Training
|
|
| Full online Library |
| Windows Server 2008 |
| |
| Windows Server 2003 |
Web Developer
|
| SQL Server |
| Help Desk Support |
| MS Office |
| CompTIA Training |
| |
| Cisco Training |
|
Other Course
|
|
| |
| |
|
|
|
|
|
|
 |
|
 |
 |
 |
|
 |
 |
 |
 |
 |
![]() |
 |
|
| |
Designing Security for a Microsoft Windows Server 2003 Network - Learning Segments |
|
|
| |
| Creating the Conceptual Design for Network Infrastructure Security by Gathering and Analyzing Business and Technical Requirements |
Analyze business requirements for designing security. Considerations include existing policies and procedures, sensitivity of data, cost, legal requirements, end-user impact, interoperability, maintainability, scalability, and risk.
- Analyze existing security policies and procedures.
- Analyze the organizational requirements for securing data.
- Analyze the security requirements of different types of data.
- Analyze risks to security within the current IT administration structure and security practices.
|
Design a framework for designing and implementing security. The framework should include prevention, detection, isolation, and recovery.
- Predict threats to your network from internal and external sources.
- Design a process for responding to incidents.
- Design segmented networks.
- Design a process for recovering services.
|
Analyze technical constraints when designing security.
- Identify capabilities of the existing infrastructure.
- Identify technology limitations.
- Analyze interoperability constraints.
|
| Creating the Logical Design for Network Infrastructure Security |
Design a public key infrastructure (PKI) that uses Certificate Services.
- Design a certification authority (CA) hierarchy implementation. Types include geographical, organizational, and trusted.
- Design enrollment and distribution processes.
- Establish renewal, revocation and auditing processes.
- Design security for CA servers.
|
Design a logical authentication strategy.
- Design certificate distribution.
- Design forest and domain trust models.
- Design security that meets interoperability requirements.
- Establish account and password requirements for security.
|
Design security for network management.
- Manage the risk of managing networks.
- Design the administration of servers by using common administration tools. Tools include Microsoft Management Console (MMC), Terminal Server, Remote Desktop for Administration, Remote Assistance, and Telnet.
- Design security for Emergency Management Services.
|
| Creating the Physical Design for Client Infrastructure Security |
Design a client authentication strategy.
- Analyze authentication requirements.
- Establish account and password security requirements.
|
Design a security strategy for client remote access.
- Design remote access policies.
- Design access to internal resources.
- Design an authentication provider and accounting strategy for remote network access by using Internet Authentication Service (IAS).
|
Design a strategy for securing client computers. Considerations include desktop and portable computers.
- Design a strategy for hardening client operating systems.
- Design a strategy for restricting user access to operating system features.
|
Design a security update infrastructure.
- Design a Software Update Services (SUS) infrastructure.
- Design Group Policy to deploy software updates.
- Design a strategy for identifying computers that are not at the current patch level.
|
|
|
|
| Creating the Physical Design for Network Infrastructure Security |
Design network infrastructure security.
- Specify the required protocols for a firewall configuration.
- Design IP filtering.
- Design an IPSec policy.
- Secure a DNS implementation.
- Design security for data transmission.
|
Design security for wireless networks.
- Design public and private wireless LANs.
- Design 802.1x authentication for wireless networks.
|
Design user authentication for Internet Information Services (IIS).
- Design user authentication for a Web site by using certificates.
- Design user authentication for a Web site by using IIS authentication.
- Design user authentication for a Web site by using RADIUS for IIS authentication.
|
Design security for Internet Information Services (IIS).
- Design security for Web sites that have different technical requirements by enabling only the minimum required services.
- Design a monitoring strategy for IIS.
- Design an IIS baseline that is based on business requirements.
- Design a content management strategy for updating an IIS server.
|
Design security for communication between networks.
- Select protocols for VPN access.
- Design VPN connectivity.
- Design demand-dial routing between internal networks.
|
Design security for communication with external organizations.
- Design an extranet infrastructure.
- Design a strategy for cross-certification of Certificate Services.
|
Design security for servers that have specific roles. Roles include domain controller, network infrastructure server, file server, IIS server, terminal server, and POP3 mail server.
- Define a baseline security template for all systems.
- Create a plan to modify baseline security templates according to role.
|
| Designing an Access Control Strategy for Data |
Design an access control strategy for directory services.
- Create a delegation strategy.
- Analyze auditing requirements.
- Design the appropriate group strategy for accessing resources.
- Design a permission structure for directory service objects.
|
Design an access control strategy for files and folders.
- Design a strategy for the encryption and decryption of files and folders.
- Design a permission structure for files and folders.
- Design security for a backup and recovery strategy.
- Analyze auditing requirements.
|
Design an access control strategy for the registry.
- Design a permission structure for registry objects.
- Analyze auditing requirements.
|
|
|
|
|
|
|
|
|
 |
 |
 |
 |
 |
|
|
|
 |
 |
 |
 |
|
|
 |
![]() |
 |
|


|
 Full
motion video
Full
motion video
Each class is presented in
full motion video allowing
you to see the steps, hear
the explanations, and perform
the tasks which includes our
interactive hands-on training
simulations, students will
learn from real-world scenarios
taught by our expert instructor.
 Instructor-Led
Training
Instructor-Led
Training
Combines both the convenience
and affordability of computer-based
training with the effectiveness
of a traditional classroom
setting. The instructors featured
in our multi-media DVD's are
not only certified in their
area of expertise, but also
have years of real world experience
and are subject matter experts
in their fields. |
 |
 |
 E-BOOKS
(PDF) E-BOOKS
(PDF)
We supply a complete line
of e-books to offer a complete
training solution. Our courses
include e-books for CompTIA,
CISCO and Microsoft certifications.Supplied on DVD for DVD courses or downloadable for Online Courses. |
 |

|
 Practice
Exam Simulators Practice
Exam Simulators
We offer
exam simulators for
all technical certifications.
Our exam simulators
are the closest replication
to the real exam!
Our exam simulators creates
a simulation of an actual
certification exam. Under
timed conditions, IntelliSage?
sets up a test with 60
randomly chosen questions
designed to help you get
ready for the real exam.
As with the Practice Exam,
the Certification Simulator
allows you to mark questions
you cannot answer for
review at the end of the
test.
If you ask, IntelliSage?
will show you the correct
answer. IntelliSage? will
also explain why it is
the correct answer when
you select the "Learn
Now" feature. The Practice
Exam is the first IntelliSage?
step in getting you ready
to pass your certification
exams. |
 |
 |
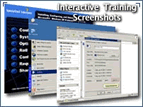 |
 Hands-on
Lab Simulation Hands-on
Lab Simulation
Hands-on Lab Simulation
is a crucial component
of your IT training. Practice make perfect. Step-by-step hands-on
labs with detail instructions
are included to reinforce
all key concepts. When
you complete a topic,
choose the Lab Simulation
button to select the associated
hands-on lab exercises.
Labs allow you to reinforce
concepts by performing
the tasks you've just
learned.. |
 |
 |
 |
 Free
Upgrades Free
Upgrades
A unique benefit of the our
Learning System, is that
it allows you to stay current
with the ever-changing certification
requirements. When a certification
test changes and we produce
an upgrade for the certification
program, we offer our customers
free upgrades on their interactive
DVD's for up to 1 year
from date of original purchase?
absolutely free! |
| |
|
|
 |
MCP 70-298 Training Course |
|
|
|
|
|
|
|
|
|
|
|
|
 |
|
|
|
|
 |
 |
 |
|
|
 |
|
 |
 |
 |
|
 |
 |
 |
|
|
 |
 |
 |
 |
 |
 |
|


